11.7.4 Transcript hash
Alice and Bob use transcript hash – the hash value of the transcript of TLS handshake messages – for many cryptographic computations in TLS. The value of the transcript hash is computed by first concatenating the handshake messages and then applying a hash function to this concatenated value:
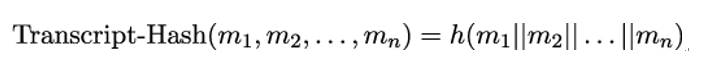
where m1,m2,…,mn are the TLS handshake messages and h is a hash function.
More precisely, the following handshake messages – but only those that were actually sent – are used in the following order as input for the transcript hash:
- ClientHello
- HelloRetryRequest
- ClientHello
- ServerHello
- EncryptedExtensions
- Alice’s CertificateRequest
- Alice’s Certificate
- Alice’s CertificateVerify
- Alice’s Finished
- EndOfEarlyData
- Bob’s Certificate
- Bob’s CertificateVerify
- Bob’s Finished
What, in general, is the use of a transcript of a cryptographic protocol? After a protocol run is finished, the transcript allows Alice and Bob to explicitly verify that they both saw the same messages being exchanged. This, in turn, creates an additional hurdle for Mallory to mount a man-in-the-middle attack by sending Alice a message mi and Bob a different message mi′.
11.7.5 Hash functions in TLS key derivation
Recall that in order to derive TLS session keys, Alice and Bob use HKDF defined in RFC 5869 (specifically, its HKDF-Extract and HKDF-Expand functions) as well as the following two functions:
HKDF-Expand-Label(Secret, Label, Context, Length) = HKDF-Expand(Secret, HkdfLabel, Length)
and
Derive-Secret(Secret, Label, Messages) = HKDF-Expand-Label(Secret, Label, Transcript-Hash(Messages), Hash.length)
The hash function used in Transcript-Hash, HKDF-Extract, and HKDF-Expand is the hash algorithm defined in the TLS cipher suite.Hash.length is the output length of that algorithm in bytes. Finally, Messages means the concatenation of the TLS handshake messages transmitted by Alice and Bob during that specific handshake session. The HkdfLabel is a data structure shown in Listing 11.7.
Listing 11.7: The HkdfLabel data structure
struct {
uint16 length = Length;
opaque label<7..255> = “tls13 ” + Label;
opaque context<0..255> = Context;
} HkdfLabel;
11.8 Summary
In this chapter, we learned how hash functions and message authentication code work, what mathematical properties they have, and how to construct them. Moreover, we covered several popular mechanisms, such as HMAC and the SHA-256, SHA-384, and SHA-512 algorithms from the SHA-2 hash algorithm family. Last but not least, we looked into the application of hash functions and message authentication code in the TLS 1.3 handshake protocol.
This chapter introduced the last building block required to understand how the TLS handshake protocol works in detail. Congratulations: you now know what Alice and Bob actually do to establish a TLS session!
In the next chapter, we will wrap up TLS 1.3 handshake. To do this, we will zoom out of the cryptographic details and give a higher-level description of TLS handshake using state machines for the TLS server and TLS client, which are specified in RFC 8446. Moreover, we will show how you can use s˙client, a TLS client program from the popular OpenSSL toolkit, to conduct your own experiments with TLS.