12.3.1 HKDF-Extract
HKDF-Extract, or HE for short, implements the first stage of the HKDF, which takes the keying material as input and extracts a fixed-length pseudorandom key K from it. In particular, it is involved in the derivation of the handshake secret SH and the master secret SM (see Figure 12.9 and Figure 12.11, respectively).
HKDF-Extract is illustrated in Figure 12.3. It takes two inputs: a salt and an input keying material (IKM). The salt is a non-secret random value. If no salt is provided, HKDF-Extract takes a string of zeros of the length equal to that of the hash function output. HKDF-Extract outputs a pseudorandom key (PRK). The PRK is calculated as PRK = HMAC-Hash(salt, IKM). Since HKDF-Extract is based on the HMAC construction, which is in turn a construction template that can use different hash functions [103], HKDF-Extract can also use different cryptographic hash functions.
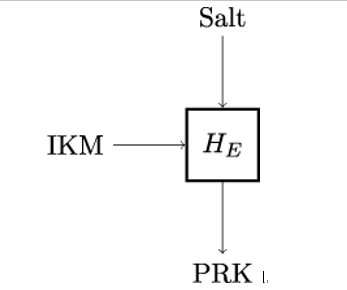
Figure 12.3: HKDF-Extract function used for TLS key derivation
A new TLS secret is derived using HKDF-Extract with the current TLS secret state as salt and the PSK – established out of band or derived from the resumption˙master˙secret instance of a previous TLS session – or the DHE or ECDHE based shared secret that Alice and Bob have established during the current TLS handshake as IKM.
12.3.2 HKDF-Expand
The second stage of the HKDF function expands a PRK to a pseudorandom bit string of the desired length, which can then be used to derive secret keys. HKDF-Expand is illustrated in Figure 12.4.
HKDF-Expand takes three inputs: a pseudorandom key PRK (which must have at least the length of the output of the hash function used), an optional context and application-specific information info, and the desired length in bytes of the output keying material L.
The output of HKDF-Expand is an L-byte long Output Keying Material (OKM). The OKM is calculated by first calculating the following N values, where N is the result of the ceiling function applied to (L∕HashLen):
T(0) = empty string(zero length)
T(1) = HMAC-Hash(PRK,T(0)|info|0x01)
T(2) = HMAC-Hash(PRK,T(1)|info|0x02)
…
T(N) = HMAC-Hash(PRK,T(N − 1)|info|N)
where | denotes the bit-wise concatenation. The HMAC construction for key-dependent hash values is explained in Section 11.5, Message authentication codes. After that, the OKM is built by taking the first L octets of T = T(1)|T(2)|…|T(N).
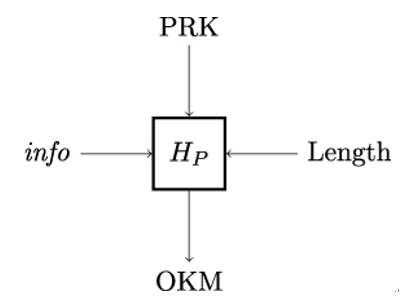
Figure 12.4: The HKDF-Expand function HP
After each invocation of the HKDF-Extract function, the HKDF-Expand function is invoked one or more times.