12.1 Key establishment in TLS 1.3
Using the TLS handshake protocol, Alice and Bob negotiate the cryptographic algorithms and key sizes. They also exchange the key shares that are required to establish the master secret. Further context-specific shared secrets and keys are then derived from this master secret according to TLS 1.3’s key derivation schedule. The secure communication channel is based on a subset of these derived secret keys.
The basic principle of TLS key establishment is shown in Figure 12.1. First, Alice and Bob negotiate cryptographic algorithms, key sizes, and exchange key shares. In the second step, Alice and Bob derive a number of context-specific TLS secrets, and in particular, a shared master secret. Each secret depends on the keying material as well as the label and the context used as inputs to generate that secret.
Finally, in the third step, Alice and Bob use the TLS secrets to derive a number of keys according to TLS 1.3’s key derivation schedule. Because the derived TLS secrets are context-specific, no further labels or additional information is needed to derive the TLS keys. However, due to context-specific secrets as input for the key derivation, the secret TLS keys are also context-specific:
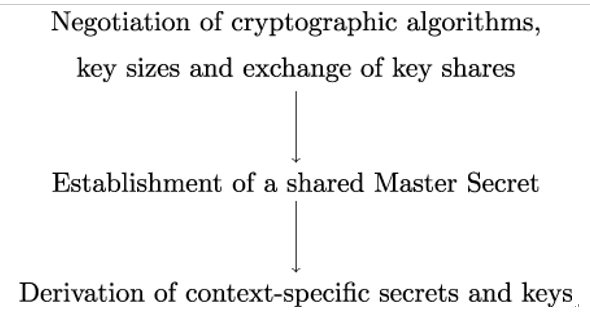
Figure 12.1: A high-level view of key establishment in TLS 1.3
We will cover each of the three steps shown in Figure 12.1 in detail. As we have seen, the first step, exchange of key shares and establishment of a shared master secret over an insecure channel, can only be accomplished using a good deal of math, which is explained in Chapter 7, Public-Key Cryptography. In the present chapter, we will focus on TLS 1.3’s key derivation schedule, that is, the process of deriving further, context-specific secrets and keys from an initial secret.
12.2 TLS secrets
We saw in Chapter 3, A Secret to Share, that a good cryptographic system has multiple keys so that every key is used for a single purpose only. TLS is no exception, and in this chapter, we are going to discuss in detail what cryptographic keys client Bob and server Alice need to establish a secure TLS channel.
However, before discussing the cryptographic keys, we first need to understand what TLS secrets are and how they are derived. TLS uses a three-step approach for generation of cryptographic keys, in which the keys are generated from the secrets:
- Alice and Bob first establish a shared master secret.
- They derive context-specific secrets from the master secret.
- Finally, they derive context-specific keys from these derived secrets.
Note that there is no conceptual (or cryptographic) reason to differentiate between secrets and keys. But because the TLS 1.3 specification uses this terminology and we want to provide a trustworthy guide to this specification, we felt the need to do the same differentiation here.
Table 12.1 gives an overview of secrets used in the TLS protocol and briefly explains their purpose. Don’t worry if the sheer number of TLS secrets looks overwhelming at first.
To help you, we compiled a series of graphics illustrating how the specific TLS secrets and TLS keys are interconnected. You will find the graphics at the end of the next section, Key derivation functions in TLS. In the remainder of this section, we are going to look into every TLS secret in more detail.
| Secret | Purpose |
| Early secret | Used to generate key material if Bob and Alice use a pre-shared key (PSK) for their TLS handshake. |
| Binder | Establishes a binding between the PSK and current TLS handshake. |
| Early traffic secret | Used by Bob to encrypt early handshake traffic if the PSK is used for the TLS handshake. |
| Exporter secrets | Secrets that can be used outside of the TLS protocol to derive additional secret keys for higher-layer protocols or applications running on top of TLS. |
| Derived secrets | Intermediate secrets used as salt arguments for deriving TLS secrets. |
| Handshake secret | This secret is the result of the handshake. It is either derived from the early secret in case a PSK is in place or from a Diffie-Hellman key exchange between Alice and Bob. It is used as input to generate the following two TLS secrets: Bob’s handshake traffic secret and Alice’s handshake traffic secret. |
| Handshake traffic secrets | Used to generate TLS handshake traffic keys, one for Bob and one for Alice. |
| Master secret | Used as input to generate the following two TLS secrets: Bob’s application traffic secret and Alice’s application traffic secret. |
| Application traffic secrets | Used to generate TLS application traffic keys. Like with handshake traffic keys, one key is for Bob and one is for Alice. |
| Resumption master secret | Used for session resumption. |
Table 12.1: Overview of secrets used in TLS (see also [53])
Leave a Reply